Being Vigilant on Free Claims
Free claiming coins in Crypto is great, who doesn’t like free money, right? It’s also a fantastic on-boarding tool for new tokens, especially if the coins either have value on the market already or are heavily suspected to gain value after a project goes live.
Unfortunately, lots of people are scared to connect their wallet via Metamask, click through the buttons and get their free tokens because they aren’t sure if the dApp is going to drain their wallet or otherwise un-safu their funds.
So how can you know what is safe to free claim and what isn't? How about which transactions are safe to approve and which ones you should avoid or being very skeptical about? There’s a few different things going on here, so let’s break it down.
Connecting your wallet to a dApp
This is often the first step in interacting with web3 stuff. You approve a website to read your balances, suggest transactions, lots of pretty harmless stuff (with regards to your wallet, mind your privacy concerns though) necessary to interact with the application.
Metamask Approvals
This is one of the easiest things your average crypto user can do. When you are use a dApp, you must explicitly approve or deny them specific allowances (think permissions) which they prompt you for a decision. Now there are two different things you can approve and revoke as needed for dApps: connection with the dApp itself and and approvals you have granted for it to interact with your wallet. As explained in further detail here and on this twitter thread, when you disconnect your wallet, you effectively revoke the permission for it to see your public address, token balances, ask you to confirm transactions, etc. Revoking an approval / allowance ensures the dApp cannot interact with your wallet anymore.
This article has a great quote for how to think about these things.
“Approving Allowances means authorizing the smart contract, in advance, to spend the tokens, without needing the private key to do that. Of course, a legit smart contract (such as Uniswap, Maker, Aave and all the most popular dApps), not developed with scam purposes in mind, would not provide in its code the opportunity of arbitrarily spending user’s tokens. However, the problem arises when you approve Allowances for little-known smart contracts, perhaps not subject to audit and peer review of the code.”
Also this post and presentation, “Unlimited ERC20 Allowances Considered Harmful” is an excellent resource to understand how this stuff works.
“With Ethereum's native ETH token it is possible to call a smart contract function and send ETH to the contract at the same time. This is done using so-called payable functions. But because ERC20 tokens are smart contracts themselves, there is no way to directly send tokens to a smart contract while also calling one of its functions.“
EIP-2612 (Permit) as mentioned in the presentation may also be useful in making security in this area better as well.
In general, you should avoid approving any “unlimited” permissions for dApps, as it increases your wallet’s attack surface. The reason they exist is to make it cheaper, save on the number of transactions and so on, but they come with the security trade-off. There are some common use cases that may require (or encourage) such approvals though, such as NFT platforms like OpenSea or depositing DAI using the Aave platform that may ask for “Unlimited Spend” for better usability. But you’re essentially trusting that these platforms and contracts won’t ever have a critical bug, because if they do, it could result in loss of your funds as you have granted them access to your wallet.
Try to only approve specific spend limits as much as you can instead of unlimited spend approvals in scenarios where it makes sense for you.
You can revoke permissions as well using revoke.cash or Etherscan’s Token Approval portal, although the language they use on there is not quite clear for the average user nor does Metamask have revocation abilities built into the app (yet). There’s lots of work to do to on the UI and precise wording to make disconnecting and revocation easy for Joe Crypto.
What’s the different between Disconnecting a dApp and Revoking an approval?
“Disconnecting your wallet from a dapp involves cancelling permission for it to see your public address and your token balances, and, depending on what you originally consented to, stopping it from initiating transactions (although not executing them) and viewing past activity.
Revoking an approval/allowance means a dapp can no longer access the contents of your wallet and move them around.”
Check out this article for more info.
You can also go here to see how ERC20s are created with lots of technical details. Also, there are more great resources on allowances here and here.
Making sure you have the right contract
Talking with @Hex1stentialist recently on an episode of the RHMax show, he mentioned an attack called Ice Phishing as Microsoft further details how it works here. Basically you need to check at least the last 3-4 hexadecimal characters of the contract address on Etherscan with the contract address shown on the Metamask prompt.
If they don’t match, DO NOT CONTINUE WITH THE TRANSACTION.
For example, with PLSD the contract address is 0x34f0915a5f15a66eba86f6a58be1a471fb7836a7 on Etherscan. If I see 0x34f0915a5f15a66eba86f6a58be1a471fb784459 on the Metamask prompt, I will reject the transaction, double check the website and domain I’m on and ask why in the world am I interacting with a difference contract than I expected.
Check if the Contract has been audited
There’s a couple of things here. You see a little green check mark beside “Contract Source Code Verified”, that just means that the contract code does match what’s running on the blockchain. Now, to see if anyone has submitted a formal audit report, look for “Audit Report” in green near the Contract Source Code area. It’s not an immediate red flag if there is no public audit report, and doesn’t mean the code hasn’t been audited privately necessarily, but if it has a report viewable, it’s always a plus. See the HEX contract for example.
It would be even better if platforms would, in addition to providing smart contract audit reports, provide at least the results of security assessment reports or otherwise audit reports of their platform, infrastructure, etc as these play a big role in the security of the entire product for users. Bugs in smart contracts are one thing, but security bugs in the platform itself that runs on the Internet, uses cloud services and so on are a huge part of the security picture as well.
Verify the Contract function is as expected
When you initiate a transaction and call a contract function, sometimes Metamask is useful and tells you what function it’s calling and sometimes it does not. If it tells you the function it’s calling, and you can map that to the function in the code that’s is the one that makes sense, it can give you a little bit more certainty that things are going ok.
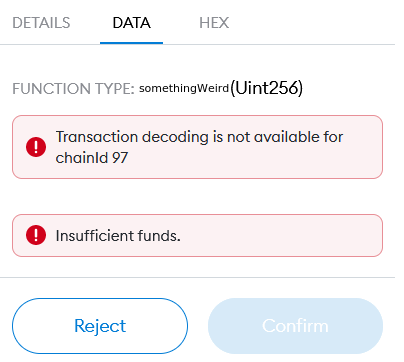
For example, if you’re doing a free claim and get a Metamask approval prompt, click on the DATA tab (to the right of DETAILS) and see FUNCTION TYPE: somethingWeird, instead of mintTokens or something else you would expect to see. Many times it may just say “Contract Interaction”, which is not very helpful for us, but other times it may actually provide the function name and other details.
Now you shouldn’t just rely on a reasonable sounding function name to call it legit, as scam contracts may try and make it look less suspicious as well, but you can go view the contract code on Etherscan, search for the function it’s presenting and decide if it both maps to the one you see and it makes sense to call this type of function within the context of a free claim, mint, whatever operation you are trying to complete.
Read the Code
If you’re not a developer, it probably isn’t going to be fun or productive for you to dive into the code with hopes it will result in a comfortable feeling afterwards or a insta-scam detection alert. You’re more than likely going to click it, scroll through, feel confused and leave it. That’s fine! Check with developers you know and trust to check the contract code out instead.
There’s also attacks like using a proxy contract for delegation, which is meant for upgradability of the contract, but can be used as a sort of misdirection technique. It’s basically where the contract your reading may be using functionality described and in code elsewhere, which could be malicious. It’s more work to manually check for these types of patterns for the casual user, but if interested you can read more about them here and here or etherscan also offers a checker service that can give you some confidence.
Do hardware wallets help?
Not against these particular attacks regarding allowances and such. Hardware wallets such as Ledger and Trezor greatly reduce your attack surface and help keep your private keys more secure than they would be by simply using Metamask on your computer. That’s because if you ever had malware on your computer, which could access your wallet, it might be game over. Hardware wallets are not a full computer, but a tiny computer with wallets on them, so malware isn’t really a problem for them (yet). So everybody recommends using a hardware wallet, for good reason, but come to terms with what they do and what they don’t do: they aren’t the solution for everything and they aren’t meant to stop every single attack out there. But they do a good job against most of them.
So that’s it! Got any more tips for how to avoid free claim scams by checking the code or functions within Metamask? Let me know on twitter and go forth and stay safe out there!